Before doing anything for real just a reminder why you should be concerned enough to put in the extra work. Running any kind of code on your computer, tablet or smart phone is risky. Bad code can spin up your CPU in never ending loops. That is nearly a threat from the past as todays threats are about your identity, your bank account or your pay service your device control or your device joining a bot net as a controlled device.
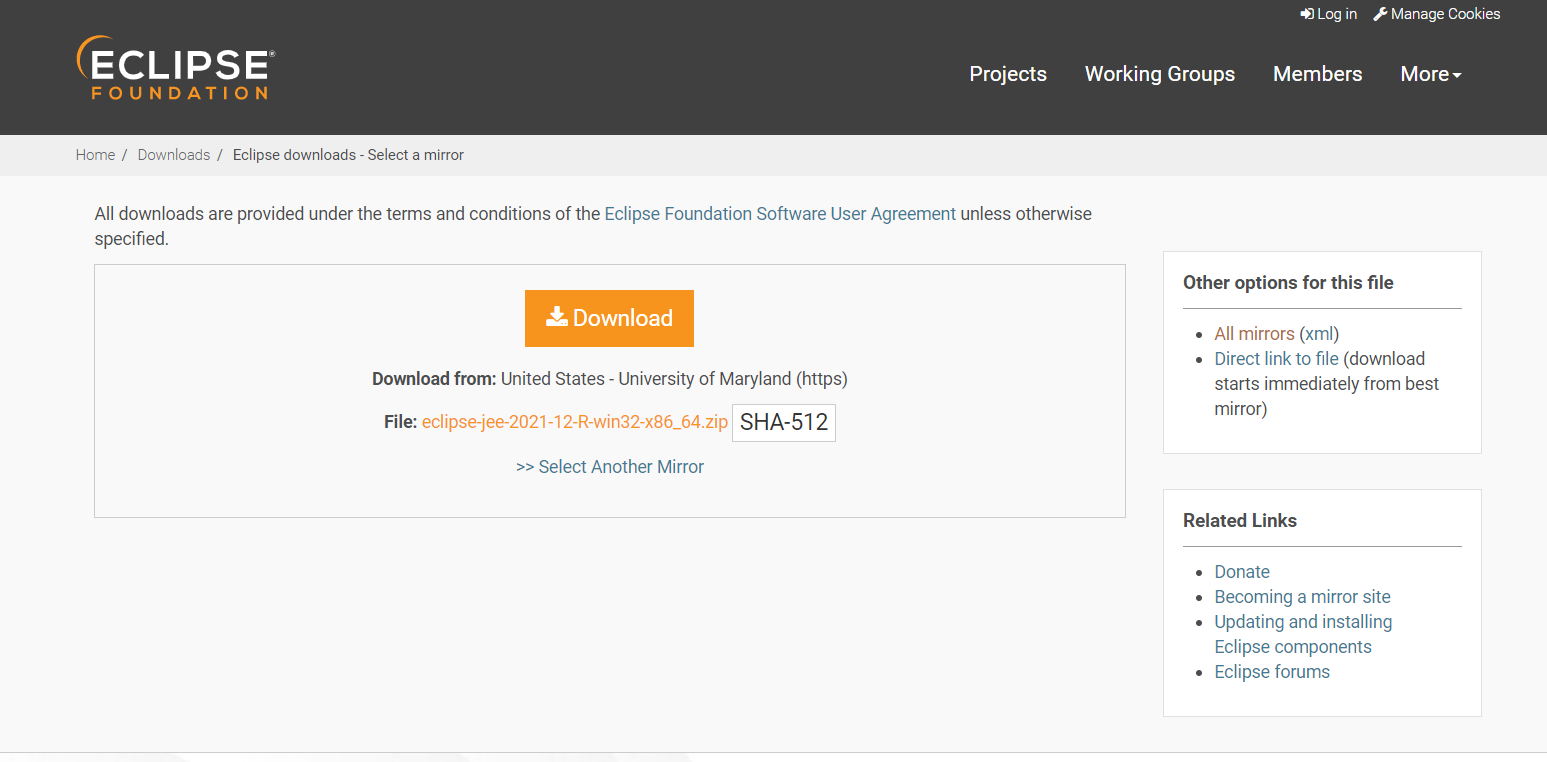
The internet security is all about trust and chain of custody. When communicating with a website or service there is the server certificate that should gurantee the identity of provider of that file. So for example you want to download the latest version of the Eclipse IDE installer with the WTP extensions
In open Source distribution one finds usually a central repository of that projects binaries and source code and than satellite
sites that present a mirror of the files for download.

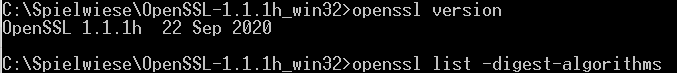
There are different tools to create a hash - the standard open tool is openSSL. OpenSSL is a open source
project that does not distribute binaries or builds, but just source.
When looking for binaries for ports for Windows, Linux and Mac OSX you will have to use your favorite search engine. Just remember that cryptography is still
considered illegal in certain jurisdictions.

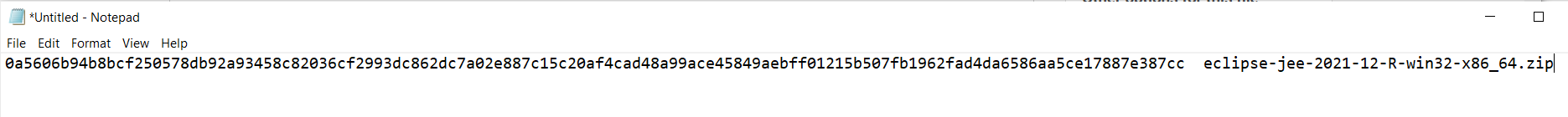
If you are a comfortable Windows type your can use the power shell tool Get-FileHash
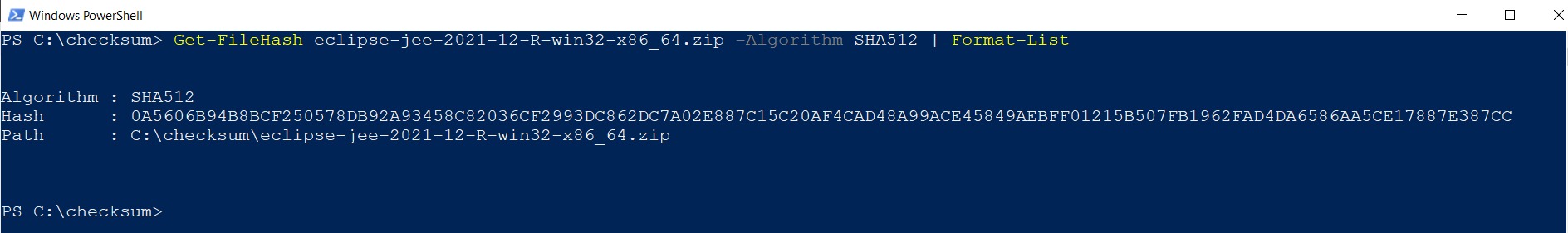
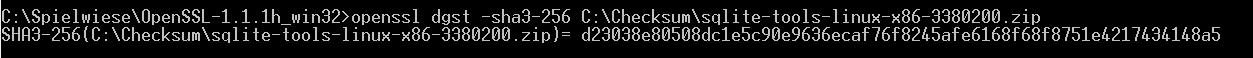
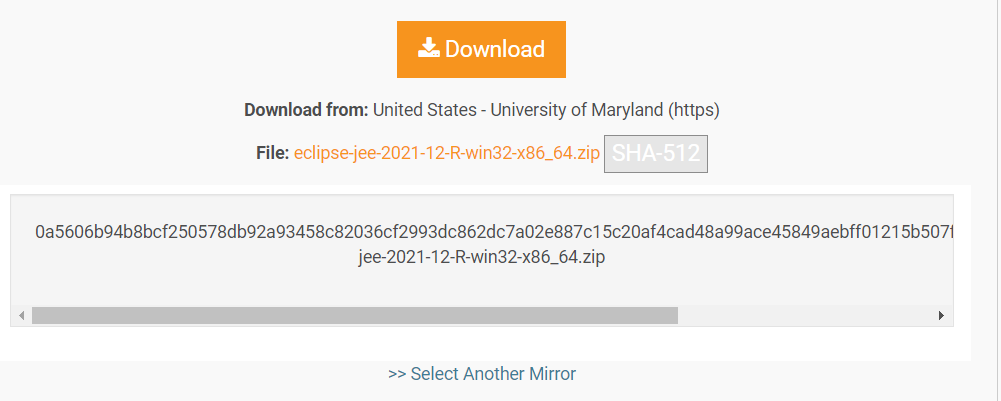
Compare the recorded website hash with the generated hash and you can be fairly sure that you downloaded an unchanged file from the server.
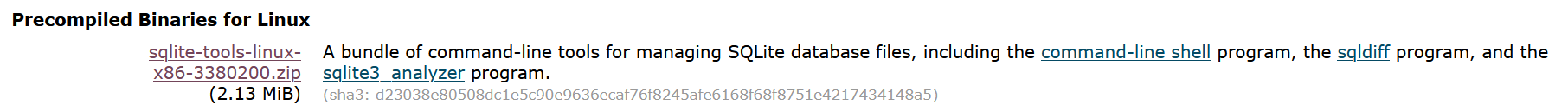
In the case of downloading SQLite from SQLite download one finds a new
challenge in the form of a new algorithm that the website calls sha3 and in this specific case is actually a sha3-256 digest.
The new part is here that this new algorithm is not available in openssl in versions lower than 1.1 and not available
at all in the Windows PS tool Get-FileHash.
For the digest of these specific download files one finds this new algorithm sha3. What makes this designation even
more cryptic is that we are not told about the actual digest length. The displayed digest length of 64 hex numbers which
equals 256 actual bits gives an informed person the clue that we are dealing with a sha3-256 digest algorithm.
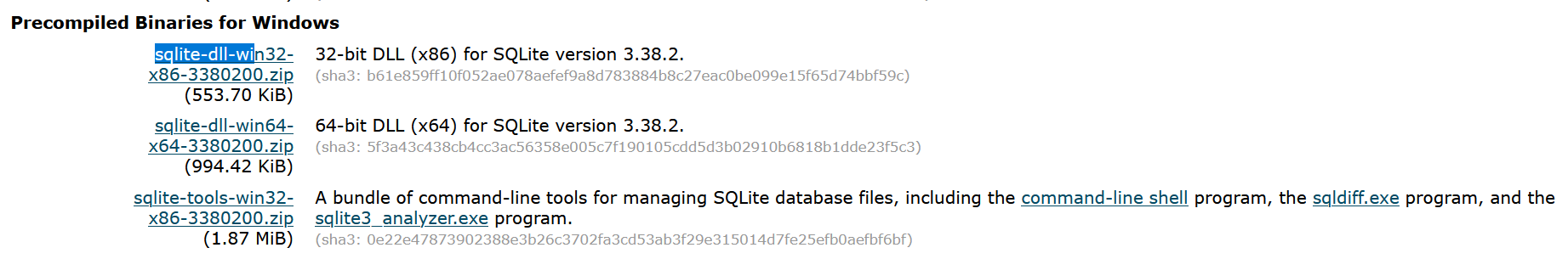
Compare the recorded website hash with the generated hash and you can be fairly sure that you downloaded an unchanged file from the server.

Sadly, I have to report at the end of this simple exercise that the SQLite download page on 3/30/2022 for the windows precompiled 64-bit dll is not creating the right digest. So we either have a case of changed binaries or of a lack of diligence when it came to the update of the web page digest information or we have a failed download - I did repeat download and test of digest a few times - or a security breach.
I checked the Linux binaries next - the Linux community in general is more security conscious - here all is good.
The web page download shows: